Phishing Simulation
What is a Phishing Simulation?
A Phishing Simulation is a method used to test the susceptibility of users in your organisation to phishing attacks. Phishing attacks involve contacting unsuspecting victims (usually via email) in an attempt to persuade them into performing an action or divulging sensitive information to the attacker. Phishing Simulations use the same techniques as actual threat actors, such as social engineering, without the actual risk of harm to the user or organisation. A Phishing Simulation engagement (also known as a Phishing Campaign) can use several techniques, including:
- Encouraging a recipient to click on a hyperlink to a website.
This is known as a phishing link. The linked website will be a fake version of a real website, and any information, including usernames and passwords, will be captured by the team running the campaign. - Encouraging a recipient to open an attachment.
A file attached to the email can report back to the campaign if opened by the recipient. This technique simulates the execution of malicious attachments, such as ransomware, key-loggers, or viruses. - Encouraging a recipient to divulge sensitive information.
Phishing emails may simply ask the recipient to respond with sensitive information, such as financial information, user credentials, or commercially sensitive information. The team running the campaign will receive the reply.
The overall goal of a Phishing Simulation is to educate users on how to identify and avoid phishing attacks and to raise awareness of the risks associated with phishing. By simulating a real-life phishing attack, users and organisations can learn how to recognise common phishing tactics, such as email spoofing, suspicious URLs, and requests for sensitive information.
How do Phishing Simulations work?
Some email hosting providers have Phishing Simulation capabilities built-in, however, there are also stand-alone phishing platforms that can be used to operate phishing campaigns. These platforms are used to develop phishing email templates, and landing pages and send emails to recipients, tracking the results.
Our Methodology
Endure Secure’s typical Phishing Simulation methodology consists of the following:
- Determine the scope.
We will meet with you to discuss the campaign specifics, such as the recipients, email templates, landing pages, difficulty, and schedule. - Develop phishing emails and landing pages.
Realistic phishing emails and phishing landing pages will be developed to suit your organisation. - Configure email filters.
We will assist you with safely configuring your email security settings so that our phishing emails are not blocked. This is because the point of the campaign is to test your recipient’s resilience to phishing attacks rather than any technical controls. - Schedule and run the campaign.
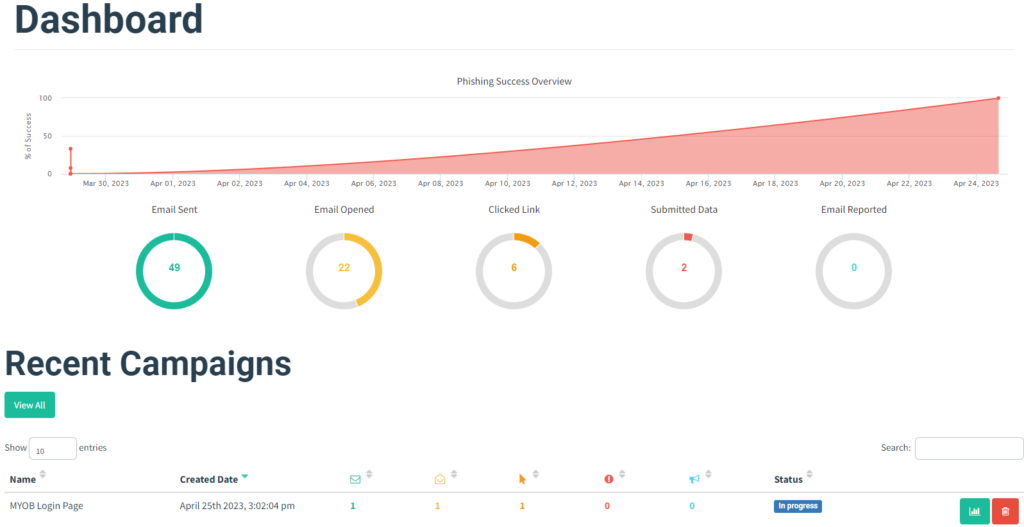
A typical campaign will run over a few weeks, with several emails sent to each recipient. - Produce a report.
A detailed report will be developed and delivered, with detailed statistics of the campaign including emails opened, clicked links, data submitted, and emails reported. - Provide a debriefing.
We will meet with your organisation to go over all findings and recommendations of the phishing campaign.
What makes a good Phishing Simulation Campaign?
A good Phishing Simulation email should closely mimic a real phishing email in order to test the recipients’ ability to detect and respond appropriately to the attack. At the same time, you may wish to intentionally introduce some suspicious indicators into your phishing emails to give your users a chance to identify and report them. Here are some key elements of a good phishing simulation email:
- Sender: The sender address should appear convincing, often using a fake domain name that is very similar to a real one (also known as typosquatting).
- Urgency: The email should create a sense of urgency, requiring immediate action from the recipient such as clicking a link or downloading an attachment.
- Social Engineering: The email should use social engineering tactics to create a false sense of trust, such as impersonating a trusted and expected organisation, person, or service.
- Realistic Content: The email should have a believable and realistic subject line and content, including graphics, logos, and formatting similar to that used by legitimate organisations.
Overall, a good phishing simulation email should be convincing and realistic enough to fool recipients into believing it is a legitimate email but also provide an opportunity for them to learn how to avoid falling for similar scams in the future.
Should my company conduct a Phishing Simulation?
The ACSC Annual Cyber Threat Report, July 2021 to June 2022 lists phishing as one of the most common techniques that all types of threat actors used to compromise their targets. If your company has never performed any type of attack simulations, a Phishing Simulation is a great place to start. However, it is a good idea to ensure users have undergone some level of User Awareness Training to explain the dangers of phishing emails. This is because users shouldn’t be expected to identify phishing attacks (including simulated attacks) without first being made aware of them.
What are some other techniques to protect against phishing?
As well as conducting regular Phishing Simulations, there are several techniques that can help protect your organisation against phishing attacks, including:
- Education and awareness: Training employees on how to recognise and report phishing attacks is the best defence against phishing attacks. This is because all technical controls are prone to failure, with threat actor techniques evolving constantly.
- Use strong passwords: Use strong passwords, and do not reuse them on different websites or applications. A password manager is helpful in securely generating and storing unique, strong passwords.
- Multi-factor Authentication: Enable multi-factor authentication on all accounts and services that have it available.
- Email Security: Many email providers and platforms, attempt to block suspicious emails by default. Additional email security solutions, such as Email Security Gateways (ESG’s), provide even more protection by automatically following hyperlinks and detonating attachments in sandbox environments (malware analysis).
- Verify the URL of all hyperlinks before clicking: Verify the URL of the website or link in the email is legitimate, and check that it begins with “https” and has a valid SSL certificate.
- Don’t run suspicious attachments: Verify the safety of any attached files. Don’t run any executables or scripts, and do not enable Microsoft Office macros from untrusted senders.
- Keep software up-to-date: Keep all software, including operating systems, web browsers, and applications, up-to-date with the latest security patches.
Contact Endure Secure
Endure Secure is available to answer your Phishing Simulation enquiry within 8 business hours. Please include as much information as possible for your request.
Please contact us using this form, email us at [email protected], or call us on 0420 231 893.