Endure Secure Knowledge Base
Installing a Wildcard SSL/TLS Certificate on a Splunk Web (Running in a Docker Container)

The Environment
- Synology DS918+ with 12GB RAM
- Splunk 8.1.1 – Build 08187535c166
- Splunk running is running in a Docker container
Resources
I followed this guide from the official Splunk manual.
Preparation
You will need the following:
- Administrator access to your Synology NAS. I’m using a Synology DS918+ running DSM 6.2.4-25556.
- Your Private Key from your Public/Private Key Pair. It should have the file extension of .key and when opened in a text editor, should look like the following:
-----BEGIN PRIVATE KEY-----
<base 64 encoded private key>
-----END PRIVATE KEY------ Your Full Certificate Chain file. This is the full chain of certificates, starting with your certificate, then any certificate authorities in the order described below:
-----BEGIN CERTIFICATE-----
<base 64 encoded certificate>
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
<base 64 encoded intermediate certificate authority's certificate>
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
<base 64 encoded root certificate authority's certificate>
-----END CERTIFICATE------ Each of these files are in PEM format, which is just a Base64 encoded binary file so that they can be read as text files. Decoding these files will result in mainly non-printable characters. For more info have a read about Privacy-Enhanced Mail.
Installation
- Map the following volumes to a local share so that they will be persistence across container rebuilds:
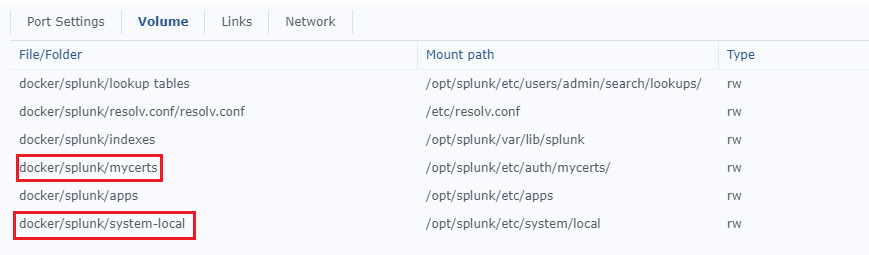
Highlighted in red is what is required for this, however I suggest mounting all of these as you will want to all these configuration files to be persistent. The indexes folder is also mapped so that the log data is persistent. - Place the Private Key and the Full Chain certificate file in the ‘mycerts’ directory.
- Edit the ‘web.conf’ file as per the docs.
[settings] enableSplunkWebSSL = true privKeyPath = Absolute paths may be used. Non-absolute paths are relative to $SPLUNK_HOME. serverCert = Absolute paths may be used. Non-absolute paths are relative to $SPLUNK_HOME. - Restart Splunk.
- Load the Splunk web interface and check.