Disable Deprecated TLS Versions on UniFi Security Gateway
Introduction
A vulnerability scan revealed that by default, an up-to-date UniFi Security Gateway supports outdated versions of TLS (TLS Version 1.0, TLS Version 1.1). As TLS versions prior to TLS 1.2 have been deprecated due to security concerns, many regulations, frameworks, and industry standards recommend or mandate that these versions of TLS should be disabled on systems.
It is not possible to disable these deprecated versions of TLS on the UniFi Security Gateway through it’s administrative web interface or through the UniFi Controller web interface. Instead, it is necessary to use Advanced Configuration. You will need to SSH into the UniFi Controller (or UniFi Cloud Key) and create a config file to disable deprecated TLS versions on UniFi Security Gateway. Full details are available in the UniFi Documentation.
Environment
The following Knowledge Base article has been written for and tested on the following environment:
- UniFi Security Gateway (USG-3P), firmware version 4.4.56.
- UniFi Controller running on Ubuntu.
If your environment differs, check the UniFi documentation.
Instructions
- Test whether your USG supports TLS 1.0/1.1 from a computer that can reach the USG by running the command:
openssl s_client -connect <usg_ip_address>:443 -tls1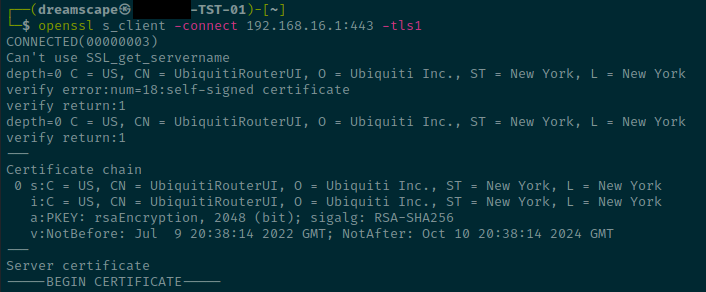
- You will see a lot of output, starting with the above, where you will see information about the TLS configuration.
- Connect to the UniFi Controller / Cloud Key that manages the USG via SSH.
- If you’ve already created a config.gateway.json, you will have to add the following configuration to it. If you haven’t already created this file, you will create it now:
- If your UniFi controller manages multiple sites, you will need to create a folder for each site where you wish the configuration to apply to. You will need to known the name of the site, which you can find out by visiting the web interface of the Unifi controller. There will be one ‘default site’, and others will be given a random string:
Default site: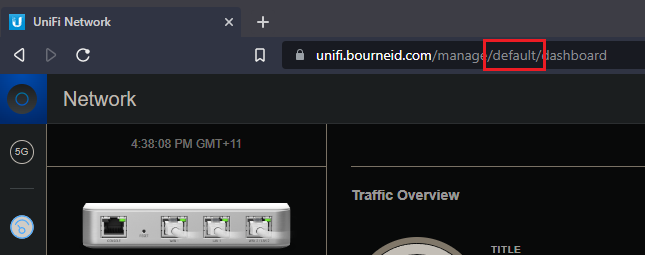
Other sites: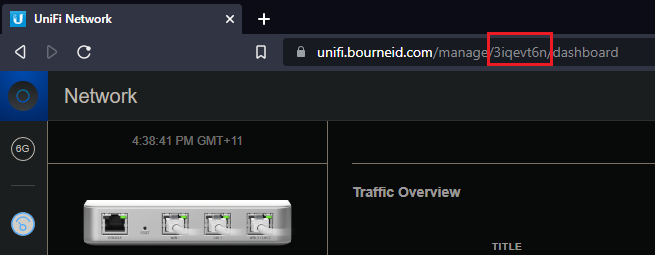
- In this example, for the default configuration you will create the config.gateway.json file in /usr/lib/unifi/data/sites/default.
- For the other site, you would create the config.gateway.json file in /usr/lib/unifi/data/sites/3iqevt6n.
- Note that the /sites folder may not already exist.
- Note that, by default, these directories and files should be owned by unifi:unifi.
- If your UniFi controller manages multiple sites, you will need to create a folder for each site where you wish the configuration to apply to. You will need to known the name of the site, which you can find out by visiting the web interface of the Unifi controller. There will be one ‘default site’, and others will be given a random string:
- The config.gateway.json file should include the following:
{ "service": { "gui": { "older-ciphers": "disable" } } } - For the USG in each site, log into the UniFi Controller web interface and go to UniFi Devices > click on the USG, > Settings > Provision > Confirm.
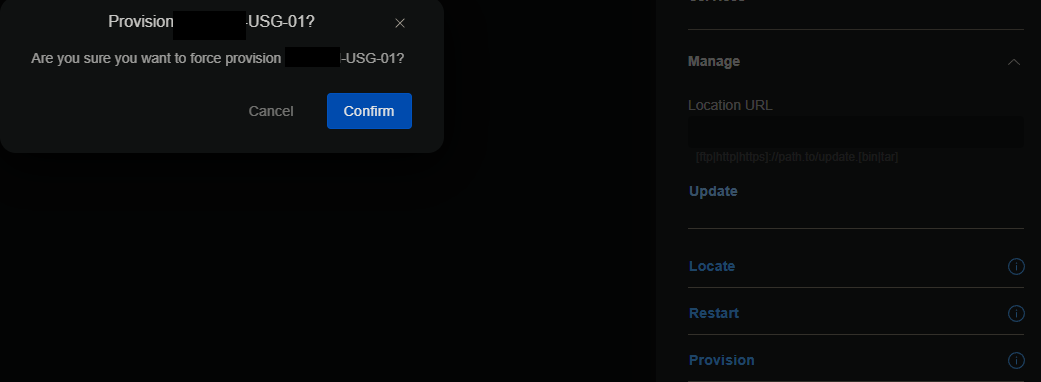
- Test again whether your USG supports TLS 1.0/1.1 from a computer that can reach the USG by running the command:
openssl s_client -connect <usg_ip_address>:443 -tls1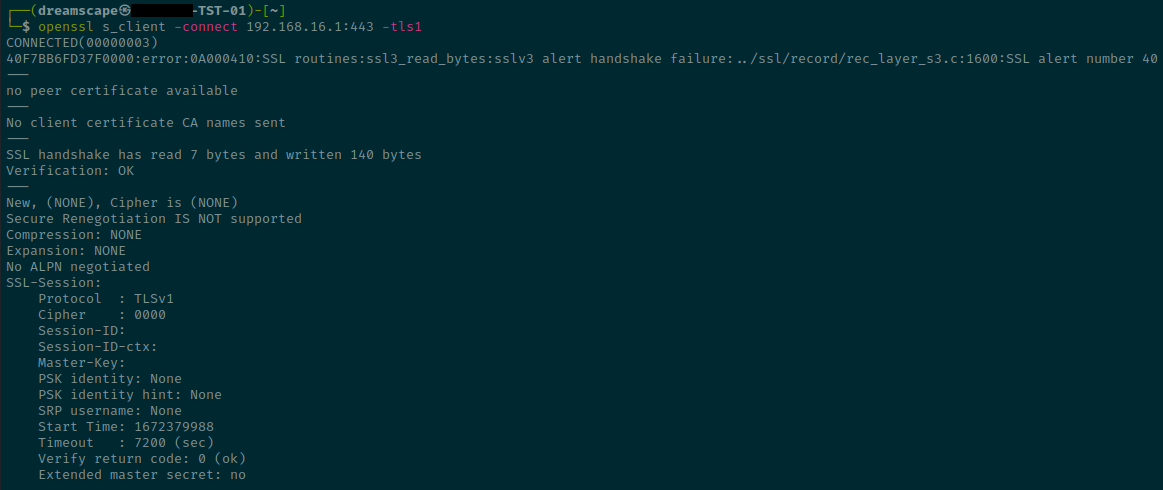
Resources
The following resources were helpful in creating this Knowledge Base Article:
- https://help.ui.com/hc/en-us/articles/215458888-UniFi-USG-Advanced-Configuration
- https://help.ui.com/hc/en-us/articles/115004872967
- https://community.ui.com/questions/How-to-disable-TLSv1-0-on-a-USG-Pro-4/4e97f5f9-b017-48d6-9457-526c9994d0e0?page=1
- https://community.ui.com/questions/Disable-TLS-1-0-and-TLS-1-1-for-management-interfaces/8b4574cc-a8c9-476f-8664-54eeb70196c1
- https://www.cyber.gov.au/acsc/view-all-content/advice/guidelines-cryptography
- https://datatracker.ietf.org/doc/html/draft-ietf-tls-oldversions-deprecate-00