Dodgy Domains and Where to Find Them
Note: This blog post contains fictional domains for the purpose of teaching underlying concepts. Many domains may also be defanged, which entails changing certain details about a domain/URL, such as wrapping a period (.) in square brackets, and substituting the letter “t” to the letter “X” in the string “http”. Defanging also extends to periods used in IP addresses. The purpose of defanging is to be able to safely share URLs/IP addresses that are potentially malicious without the risk of someone accidentally clicking on a URL/IP address which would then open the malicious site in their browser.
Background
Attackers long have employed domain spoofing techniques to carry out attacks. The more similar a malicious domain is to a genuine domain, the more likely a victim will click on a hyperlink sent via email or trust the sender of an email address, and ultimately fall victim to attacks that work by abusing their trust in a particular brand. Many Managed Security Service Providers (MSSPs) offer brand protection services to detect and alert customers when their own brand is being impersonated.
In my experience I’ve found the retail and e-commerce industry are the largest targets for this type of threat, as it’s quite common for the industry to employ high-pressure situations to drive-up sales – such as a promotion like “Get 2 for the Price of one – offer expires in 1 hour”. Attackers take advantage of these situations, as people often let their guard down when taking advantage of such offers that have a near-expiry date, and use it to steal money from customers. The short time-frame is easy to take advantage of, as most customer will interact with the site during the short time-window, which is often over before a company or security team is aware that the attack has happened, and can request a deregistration of the domain or a takedown of the associated website.
How it Works
Let’s start with the basics. The Domain Name System (DNS) resolves domain names into IP addresses (domain[.]com -> 10[.]10[.]10[.]10), which in turn allows web users to access websites, emails, and a a range of other services. When users visit website and input sensitive information like payment details, they are trust that the website belongs to the organisation that is advertised on the website. They are trusting their payment details are going to the organisation and that their details are being handled properly and securely. This is what the attacker is focusing on abusing – customer trust in an organisation/brand.
So let’s dive a little deeper into how organisations are linked to domains. Domains are registered for a small fee, often during an organisation’s start-up phase. A domain name is chosen that reflect the name of the organisation and the country/countries where the organisation operates. So an organisation called Katana based in Australia would likely register a domain like “katana[.]com[.]au”, where the website would be “hXXps://www[.]katana[.]com[.]au”. If the organisation also operates in New Zealand they could also register the domain “katana[.]co[.]nz”, with their same website available via that domain, targeted at their New Zealand customers.
To break this down further, there are three main parties involved in registering a domain:
- Registry: A domain name registry is an organisation that manages top-level domain names. They create domain name extensions, set the rules for that domain name, and work with registrars to sell domain names to the public. For example, VeriSign manages the registration of .com domain names and their domain name system (DNS), and auDA (Australian Domain Authority) manages the .com.au namespace.
- Registrar: The registrar is an accredited organisation, that sells domain names to the public. Some have the ability to sell top-level domain names like [.]com, [.]net and [.]org, or country-code top-level domain names such as [.]us, [.]ca and [.]eu.
- Registrant: A registrant is the person or company who registers a domain name. Registrants can manage their domain name’s settings through their registrar.
When a Registrant registers a domain name through a Registrar, they are paying a fee to the Registrar to ask the Registry to enter the Registrants Nameservers (and some other information) into the Registry’s database.
Anyone can use Whois to lookup the registration details about a domain name, including the domain registrar and how to report abuse. For example, below is the whois record for endsec.com.au (Endure Secure’s domain).
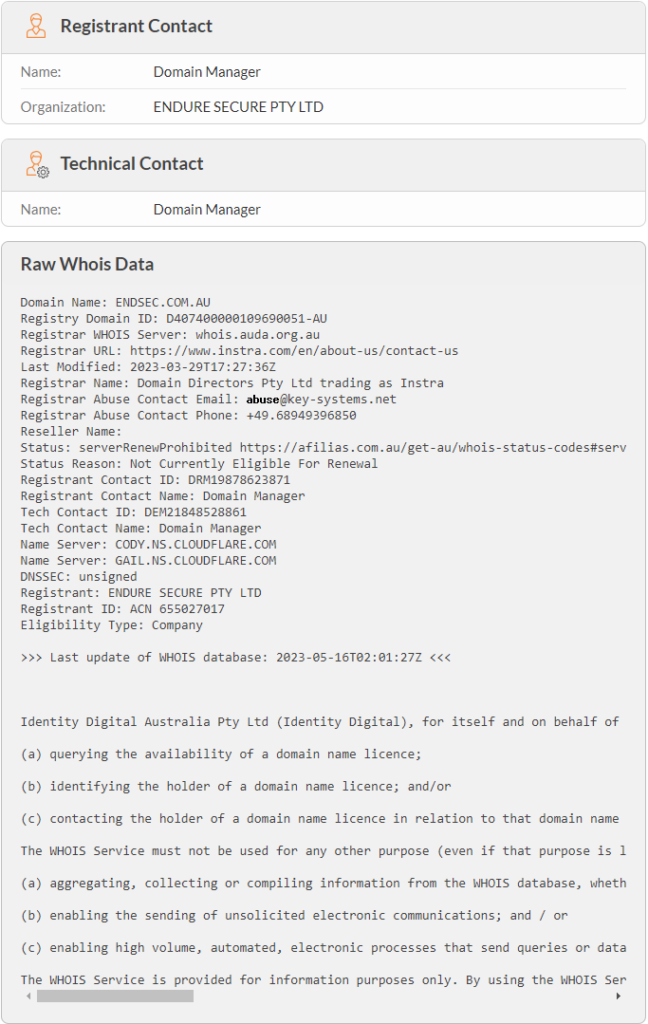
The image primarily depicts details of the registrant (Endure Secure) and Registrar (Domain Directors). As part of this you can see how to report abuse via email and over the phone.
Additionally, there are some services that allow you to perform reverse Whois lookups to identify other domains with the same Registrant Email Address or Registrant Name, such as ViewDNS. Note that reverse Whois lookup data may not always be accurate or complete as it relies on Whois data compiled over time from various sources.
One last thing to note about Whois records is the rise in domain privacy, where many registrants are allowing registrants to hide their details, which makes things more complicated, and can also aid attackers who spin up domains and don’t publish them. Take a look at this relevant article by Krebs on Security.
As we start exploring domains more, there are several terms which you may not be familiar with, the below graphic breaks down a URL (web address) and explains the different components.

Top-Level Domain Swap (TLD Swap)
Top-level domains generally fit into two groups: generic top-level domains (gTLD), and country-code top level domains (ccTLD). Top-level domains (TLDs) are overseen by the Internet Assigned Numbers Authority (IANA), a subsidiary of Internet Corporation for Assigned Names and Numbers (ICANN). IANA further delegates the management of individual TLDs to various organisations who act as regulatory bodies for the TLD.
| Group | Examples | Registry |
|---|---|---|
| gTLD | .com | Verisign |
| gTLD | .net | Verisign |
| gTLD | .xyz | XYZ |
| gTLD | .zip | |
| ccTLD | .com.au | .au Domain Administration |
| ccTLD | .co.uk | Nominet |
| ccTLD | .ru | Coordination Center for TLD RU |
These organisations, known as Registries, are tasked with stipulating any conditions for the registration of domains within the TLD, and enforcing any actions for non-compliance. For example, auDA, who regulate the .com.au TLD, have specified an eligibility criteria for registration and a policy of responding to the malicious use the TLD, which includes suspending registration.
However, not all registries are as strict on domain registration or responding to abuse, leading to some TLDs being favoured by threat actors for abuse including phishing, spam, malware, and botnets. There appears to be some corelation in malicious use of TLDs managed by developing countries, such as .pw (Republic of Palau), and .tk (Tokelau) who may not have the resources to combat abuse, or who simply need the money from the domain registration fees (at one point, one-sixth of Tokelau’s economy was made up of the sale of .tk domains).
Recently, Google has made both .zip and .mov available for registration, which has been criticised widely by the cyber security community, who suggest that this could lead to a wave of new attacks due to the ambiguity with the popular file extensions.
With such as wide array of TLDs available, an attacker could register the same domain with a different TLD, such as katana[.]co[.]uk and encourage unsuspecting customers into visiting a spoofed version of the Katana website bound to the domain that they control – which they can then use to harvest customer data, credentials, and even payment details.
The Spamhaus Project maintains a list of the Top 10 Most Abused Top Level Domains.
Look-alike Domains
A domain body is the text of the domain name that precedes the TLD. In this case the string “katana”. An attacker could register a domain against the same TLD (in this case [.]com[.]au), using a similar string. So this could include changes like:
- kataana[.]com[.]au
- kaatana[.]com[.]au
- katanaa[.]com[.]au
- kahana[.]com[.]au
Naturally these changes are quite obvious to someone who looks at the domain, but the attacker in this case is hoping that the victim would not be too attentive to the details, most likely as a result of a sense of urgency being created by the attacker. There are also Punycode attacks, which is essentially where a domain body is registered that contains a letter from outside the Latin alphabet that is meant to look the same as the domain name. To understand this below are two letters that look like the letter “a“, one is from the Greek alphabet, and the other from the Cyrillic alphabet, each are linked to a website that shows the Unicode code for each letter which you can see are different from each other, as well as the Latin alphabetic character “a“:
Now the Greek letter alpha is much more obviously different than the Cyrillic letter, but is not as obvious as an extra letter, or a different Latin alphabetic character. The letter “o” has identical characters in both alphabets that are fully identical. Below the second a has been substituted with the letter of the relevant alphabet.
| Alphabet | Altered Domain |
|---|---|
| Latin | katana[.]com[.]au |
| Cyrillic | katаna[.]com[.]au |
| Greek | katαna[.]com[.]au |
There is no visible difference whatsoever between the Latin and Cyrillic domains shown below, which is why they were so effective. However, these days browsers render domains containing non-Latin alphabetic characters in a format known as “punycode”, which make it very obvious that you’re going to a different domain.
| Alphabet | URL | Punycode URL |
|---|---|---|
| Latin | hxxp://katana[.]com[.]au/ | hxxp://katana[.]com[.]au/ |
| Cyrillic | hxxp://katаna[.]com[.]au/ | hxxp://xn--katna-6ve[.]com[.]au/ |
| Greek | hxxp://katαna[.]com[.]au/ | hxxp://xn--katna-f9d[.]com[.]au/ |
CyberChef has a punycode encoder which is worth playing around with, but it doesn’t give you the end result of what the browser will show you.
The problem here is that each domain links to a different IP address which means that despite the domain looking identical in some cases, victim are able to be directed to another website.
Hunting for Spoofed Domains
We’ve covered off some of the different ways domains can be spoofed, through making slight alterations to domains, there are also domains that are registered that will add to the existing domain, like turning katana[.]com[.]au into katanaswords[.]com[.]au. Sometimes doing this is even more effective that the techniques previously described.
In terms of how to hunt for these domains, no singular technique will find them all; therefore, a combination of techniques need to be used to hunt for spoofed domains. Many of the techniques described have been automated in Endure Secure’s freely-available, open-source, OSINT tool Scrummage.
1. Search Engines
“Have you tried Googling it?” is pretty old, yet still relevant. The best place to start is always search engines like Google. Most websites have unique characteristics in the text of the website. This usually takes the form of a company slogan, wording in a promotion by the brand, or something similar. This is often large text found on the landing page of the website. By googling this text you can often find domain spoofs as they often duplicate the entire site, words and all. This technique will only find domains that have a spoofed website attached to that domain.
2. Enumeration
Enumeration is less simple, but identifies the issue at a domain level, as a result this can help companies be able to identify potentially malicious domains, before a website is added to that domain, at which point there is a bigger threat to the spoofed organisation.
Scrummage provides all the enumeration techniques described, and hence is used for demonstrative purposes in this section of this blog post. You should also combine the techniques described for more comprehensive searching.
| Enumeration Type | Description |
|---|---|
| Purpose-Based TLDs (Scrummage Array of Values) | For the given domain, enumerate all country-specific TLDs, such as [.]gov[.]au and [.]net[.]au |
| Country-Code TLDs (ccTLDs) (Scrummage Array of Values) | For the given domain, enumerate all valid, and expired, global TLDs, such as [.]co[.]uk |
| Punycode Fuzzing of Body (Scrummage Rotor Library) | Enumerate all combinations of letters from other alphabets that resemble Latin letters in your domain name. The Scrummage Rotor library, which is also available as a standalone library here, contains an extremely comprehensive dictionary of characters from several alphabets which resemble Latin characters. The library allows you to turn on an off several flags that resemble different alphabets in use. |
Lastly, be creative, there are always gaps in enumeration, so try different combinations, try lists of brand-based TLDs that your organisation doesn’t own that could be used to spoof customers, and same for industry-based TLDs.
Responding to Dodgy Domains
Let’s say we’ve found several dodgy domains, and have confirmed that they are indeed malicious. For well-regulated TLDs, take-down requests can be requested at a registrar level. However, this can be a little more complicated for unregulated TLDs. When paired with bullet-proof webhosting services, these websites can sometimes be impossible to get removed from the internet.
For these more complicated domains, organisations can block certain TLDs; however, for customers it’s not quite so simple. At the very least, knowledge of spoofed domains, can help you spread awareness to your customers, before an attacker on a spoofed domain can target your customers.
Share this content:
